A few weeks ago, when I was going through all my online accounts and making the passwords more secure and unique I logged in to Match.com and deactivated my account. I didn’t delete it, just made it dormant. I did this because I found my Fiancée over 3 years ago (via Match.com) so there was no reason to still have an active account. I didn’t want to delete the account because it had some of our earliest messages to each other saved.
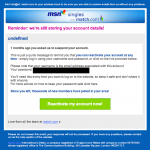
Anyway, I checked my emails today and noticed that I had one from them encouraging me to re-activate my account. What was more concerning was that the email contained my password in plain text! Here is a screenshot of the email:
I was about to submit them to plaintextoffenders.com but I did a search before and found that they were already added to the list 15 months ago, so I left a comment on the plaintextoffenders listing and decided to send a message to Match.com. The message was:
On the 20th of December 2012 I received an email encouraging me to reactivate my account. What concerns me is that in the body of the email was my password, in plain text! Firstly you should not be storing my password in plain text, and secondly (if you insist on storing passwords as plain text) you should not be sending it to me over something as insecure as email, especially if I didn’t request it!
I was about to submit match.com to http://plaintextoffenders.com, but when I searched, I saw that it was already submitted some 15 months ago. See http://plaintextoffenders.com/post/9744438766/match-com-dating-site-very-soon-after-i-got-this.
For a brief overview of why storing passwords in plain text is bad, you can start reading here: http://plaintextoffenders.com/about/
Please bear in mind that while you are now being shamed by plaintextoffenders.com, if you decide to fix the security flaw, your site would be moved to a different section of the site where you would be praised for admitting the fault and fixing it. See http://plaintextoffenders.com/reformed
I am in no way affiliated with plaintextoffenders.com, but I do support what they are trying to do and I would like to know if you are in the process of fixing, or plan to fix this security flaw in the near future?
Please reply to <email address removed>
I will update this post if/when I get a reply, but in the meantime I would recommend against joining Match.com and deleting any accounts you might have with them until they act a bit more responsibly.
Update: I got this email back from Match.com:
Thank you for contacting us at match.com.
We understand that you received an email from us on the 20th December 2012 with your password in plain text which you feel is a serious compromise of security.
We are really sorry about this error and I have forwarded your issue to our site developers to look into.
We hope you have found this information useful and please feel free to get in touch if there is anything further we can help you with. For answers to the most common questions click ‘Help’, available from the foot of any page.
At least they are not dismissing it. I wonder if anything will actually change?